PREFACE
This paper is a kind of review paper also wants Review OWASP Top 10 Security Risks, and we propose this post to develop our idea to our next post about the future serial posts that should be issued about security items(owasp top 10 list).
In one of our previous posts, we explained the site security items but in this paper, we want to give you short and fast information about the OWASP Top 10 list. The OWASP Top 10 list contains 10 top application vulnerabilities all topic of OWASP Top 10 list is very important and we have not seen any documents or references whose show the priority of them. As I had been issued in the past post, site security vulnerability has 10 items different but the OWASP Top 10 list shows us all of the standard items that we have to inspect them when we think about our site security.
WHAT IS THE OWASP?
Mark Curphey started OWASP on September 9, 2001. Jeff Williams served as the volunteer Chair of OWASP from late 2003 until September 2011. As of 2015, Matt Konda chaired the Board.
The OWASP Foundation, a 501(c) (3) non-profit organization (in the USA) established in 2004, supports the OWASP infrastructure and projects. Since 2011, OWASP is also registered as a non-profit organization in Belgium under the name of OWASP Europe VZW.
The Open Web Application Security Project (OWASP) is a 501(c) (3) worldwide not-for-profit charitable organization focused on improving the security of software. Our mission is to make software security visible so that individuals and organizations can make informed decisions. OWASP is in a unique position to provide impartial, practical information about AppSec to individuals, corporations, universities, government agencies, and other organizations worldwide. Operating as a community of like-minded professionals, OWASP issues software tools and knowledge-based documentation on application security.
Everyone is free to participate in OWASP and all of our materials are available under a free and open software license. You’ll find everything about OWASP here on or linked from our wiki and current information on our OWASP Blog. OWASP does not endorse or recommend commercial products or services, allowing our community to remain vendor neutral with the collective wisdom of the best minds in software security worldwide.
We ask that the community look out for inappropriate uses of the OWASP brand including the use of our name, logos, project names, and other trademark issues.
To bring awareness to what threatens the integrity of websites, we are continuing a series of posts on the OWASP top 10 security risks.
THE OWASP TOP 10 LIST CONSISTS OF THE 10 MOST SEEN APPLICATION VULNERABILITIES:
1-SQL Injection
Injection flaws result from a classic failure to filter untrusted input. It can happen when you pass unfiltered data to the SQL server (SQL injection), to the browser (XSS – we’ll talk about this later), to the LDAP server (LDAP injection), or anywhere else. The problem here is that the attacker can inject commands to these entities, resulting in loss of data and hijacking clients’ browsers.
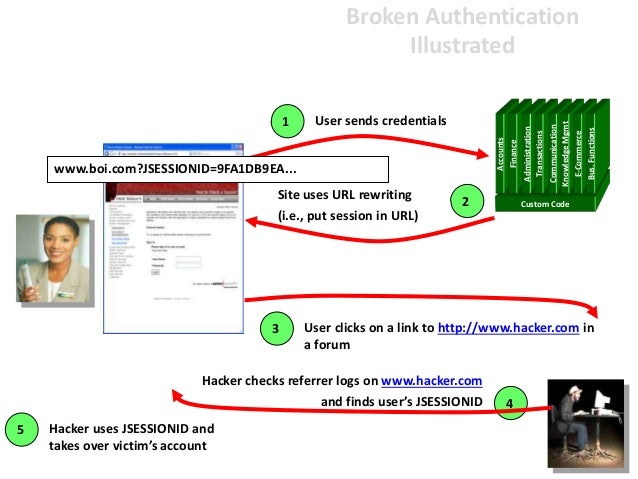
2-BROKEN AUTHENTICATION
OWASP defines Broken Authentication and Session Management as:
Application functions related to authentication and session management are often not implemented correctly, allowing attackers to compromise passwords, keys, or session tokens, or to exploit other implementation flaws to assume other users’ identities.
In other words, an attacker can get unauthorized access to a user’s data due to flaws in the implementation. Before exploiting this vulnerability you need to know a few concepts:
- why we need a Session and what a Session is?
- What a Cookie is?
- What Authentication is?
3-SENSITIVE DATA EXPOSURE
This vulnerability allows an attacker to access sensitive data such as credit cards, tax IDs, authentication credentials, etc. to conduct credit card fraud, identity theft, or other crimes. Losing such data can cause severe business impact and damage to the reputation. Sensitive data deserves extra protection such as encryption at rest or in transit, as well as special precautions when exchanged with the browser.

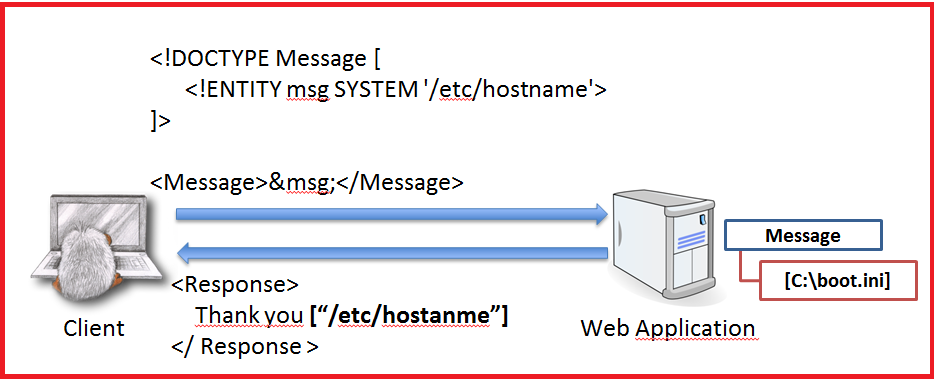
4-XML EXTERNAL ENTITIES (XXE)
XML External Entity (XXE) refers to a specific type of Server-Side Request Forgery (SSRF) attack, whereby an attacker can cause Denial of Service (DoS) and access local or remote files and services, by abusing a widely available, rarely used feature in XML parsers.
XML is a vastly used data format found in everything from web services (XML-RPC, SOAP, REST, etc.) to documents (XML, HTML, DOCX) and image files (SVG, EXIF data, etc.) use XML. Naturally, where there is XML, there is an XML parser – hold onto that thought, we’ll be coming back to it shortly.
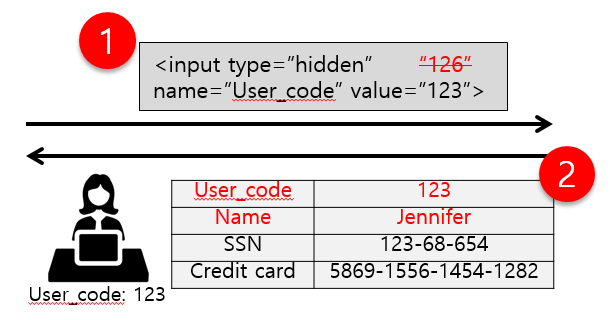
5-Broken Access control
Access control enforces policy such that users cannot act outside of their intended permissions. Failures typically lead to unauthorized information disclosure, modification or destruction of all data, or performing a business function outside of the limits of the user. Common access control vulnerabilities include:
- Bypassing access control checks by modifying the URL, internal application state, or the HTML page, or simply using a custom API attack tool
- Allowing the primary key to be changed to another’s users’ record, permitting viewing or editing someone else’s account.
- Elevation of privilege. Acting as a user without being logged in, or acting as an admin when logged in as a user.
- Metadata manipulation, such as replaying or tampering with a JSON Web Token (JWT) access control token or a cookie or hidden field manipulated to elevate privileges or abusing JWT invalidation
- CORS misconfiguration allows unauthorized API access.
- Force browsing to authenticated pages as an unauthenticated user or privileged pages as a standard user. Accessing API with missing access controls for POST, PUT and DELETE.
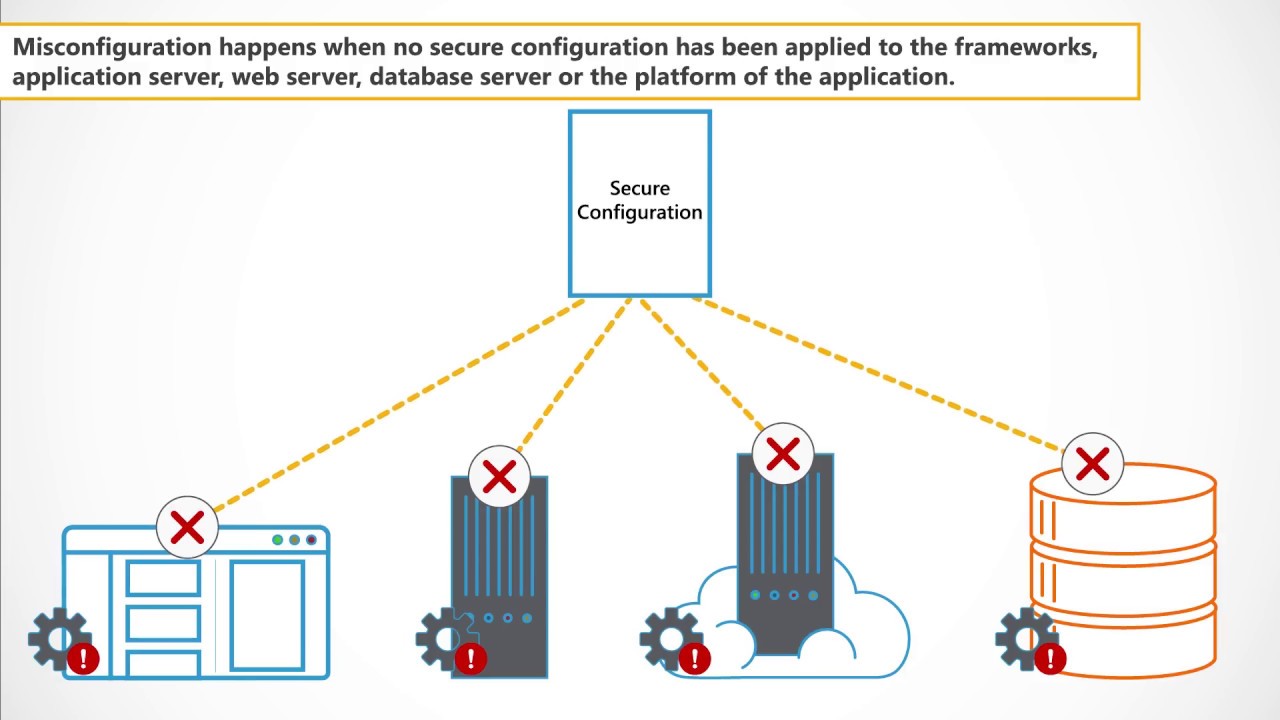
6-Security misconfigurations
Security Misconfiguration arises when Security settings are defined, implemented, and maintained as defaults. Good security requires a secure configuration defined and deployed for the application, web server, database server, and platform. It is equally important to have the software up to date.
Improper server or web application configuration leading to various flaws:
- Debugging enabled.
- Incorrect folder permissions.
- Using default accounts or passwords.
- Setup/Configuration pages enabled.
All of your data could be stolen or modified slowly over time.
Current application security architectures do not follow security by default. On the contrary, programmers must apply security measures to avoid access to private or confidential resources.
7-Cross-Site Scripting (XSS)
Cross-site Scripting (XSS) is a client-side code injection attack. An attacker aims to execute malicious scripts in a web browser of the victim by including malicious code in a legitimate web page or web application. The actual attack occurs when the victim visits the web page or web application that executes the malicious code. The web page or web application becomes a vehicle to deliver the malicious script to the user’s browser. Vulnerable vehicles that are commonly used for Cross-site Scripting attacks are forums, message boards, and web pages that allow comments.
A web page or web application is vulnerable to XSS if it uses unsanitized user input in the output that it generates. This user input must then be parsed by the victim’s browser. XSS attacks are possible in VBScript, ActiveX, Flash, and even CSS. However, they are most common in JavaScript, primarily because JavaScript is fundamental to most browsing experiences.
8-Insecure Deserialization
Most Critical Web Application Security Risks is Insecure Deserialization. This vulnerability occurs when untrusted data is used to abuse the logic of an application or application program interface (API).
For example, an attacker may go after an object or data structure, intending to manipulate it for malicious intent. OWASP listed the primary attack types as denial-of-service (DoS) attacks, authentication bypasses and remote code/command execution attacks, where attackers manipulate arbitrary code upon it being deserialized.
To fully understand insecure deserialization is we must understand both what serialization and deserialization are first. This blog will illustrate what both are in detail, as well as what insecure deserialization means, the impact of it on applications, and best practices to prevent it. We’ll then cover some solutions for preventing insecure deserialization.
9-Using Components with known vulnerabilities
These days, even simple websites such as personal blogs have a lot of dependencies.
We can all agree that failing to update every piece of software on the backend and frontend of a website will, without a doubt, introduce heavy security risks sooner rather than later.
For example, our hacked website report for 2017 has a dedicated section around outdated CMSs. This report shows that at the time of the infection:
- 3% of WordPress websites were out of date;
- 8% of Joomla! websites were out of date;
- 3% of Drupal websites were out of date;
- 3% of Magento websites were out of date.
The question is, why aren’t we updating our software on time? Why is this still such a huge problem today?
There are some possibilities, such as:
- Webmasters/developers cannot keep up with the pace of the updates; after all, updating properly takes time.
- A legacy code won’t work on newer versions of its dependencies.
This might be a little too dramatic, but every time you disregard an update warning, you might be allowing a now known vulnerability to survive in your system. Trust me, cybercriminals are quick to investigate software and update changelogs.
Whatever the reason for running out-of-date software on your web application is, you can’t leave it unprotected. Both Sucuri and OWASP recommend virtual patching for the cases where patching is not possible.
Virtual patching affords websites that are outdated (or with known vulnerabilities) to be protected from attacks by preventing the exploitation of these vulnerabilities on the fly. This is usually done by a firewall and an intrusion detection system.

10-Insufficient logging and monitoring
Logging and monitoring go hand in hand. There is little point in having adequate logs if they are not adequately monitored.
The problem of insufficient logging and monitoring covers the entire IT infrastructure and not just the internet-facing web application – as does the solution. For that reason, we will not limit this discussion to just logging and monitoring web apps.
One of the primary problems is that there are so many logs – almost all contemporary systems generate their logs. Log management thus becomes a major problem. By the time that all the different logs are gathered together and preferably collated, the sheer size of the data set becomes too large to effectively monitor manually.
The solution is in increased automation of the process. For example, some access control systems can be given their own monitoring rules. Log-on rules can be set to allow a predefined number of log-on attempts per session. The system logs the attempts, and then blocks access from that IP, either for a predefined period or indefinitely. Such systems will also likely alert the security team that something not right is happening.
conclusion:
Open Web Application Security (OWASP) is a non-profit organization but a global goal for software security. The objective is to inform individuals and companies related to the security of information systems. The organization operates as a community of like-minded professionals. Everyone is free to join the community, which today has more than 45,000 members. Each year OWASP publishes a ranking that identifies the most critical security vulnerabilities.OWASP provides a tremendous number of free resources dedicated to improving organizations’ application security posture. One of their best-known projects is the OWASP Top 10 project, which provides consensus guidance on what are considered to be the ten most significant application security risks. The OWASP Top 10 is available at https://www.owasp.org/index.php/Category:OWASP_Top_Ten_Project
OWASP offers a development guide for Web applications, which contains the best practices to adopt during the development phase of a Web project. Tools are also made available to users to perform audits of their site.



